Salient features 1. 2. 3. 4. 5.
BY UBAID SAUDAGAR
Flexible 32 bit microprocessor Address bus is of 32-bit Operating frequency of 20-33 MHz . Contains total 132 Pins. Intel’s first practical microprocessor to contain a 32-bit data bus and 32-bit memory address. 6. 16 byte prefetch queue 7. Very large address space a. 4 Gb of physical memory supported b. 64 Tb of virtual memory supported c. 4 Gb of maximum segment size 8. Integrated memory management unit 9. Object code compatible with all 8086 family microprocessors 10. High speed numeric support via 80387 11. Can operates in real, protected & virtual Mode 12. Introduced paging, virtual memory concept 13. Can operate at 11.4 MIPS. 14. Contains near about 2,75,000 Transistors.2
09-10-2012
Versions of 80386 Microprocessor
BY UBAID SAUDAGAR
(A) 80386 SX
(B) 80386 DX
(1). A.B. is of 32 Bit. (2). D.B. is of 32 Bit. (3). Total 132 Pins. (4). Can address upto 4GB of memory.
(1). A.B. is of 24 Bit. (2). D.B. is of 16 Bit. (3). Total 100 Pins. (4). Can address upto 16MB of memory. 3
09-10-2012
Pin configuration
BY UBAID SAUDAGAR
4
09-10-2012
Pin configuration cont.
BY UBAID SAUDAGAR
5
09-10-2012
Pin configuration cont. Data bus(D31 – D0): It consist of 32 data pins, therefore memory is connected in 4 banks(bank 0 – bank 3). So the 80386 can transfer 8/16/32 bit data in one machine cycle. Address bus(A31 –A2, BE3 – BE0): With the help of address lines, it is able to address 4GB of physical memory space from 00000000H to FFFFFFFFH. 4GB is connected as 4 banks of 1GB each. Therefore to address 1GB of memory, 30 address lines are required i.e. from A2-A31. BY UBAID SAUDAGAR
6
09-10-2012
Pin configuration cont.
BY UBAID SAUDAGAR
Lower two address pins A1 and A0 are internally decoded by 80386 to generate 4 bank enable signals(BE3 – BE0) BE0 applies to D7 to D0 BE1 applies to D15 to D8 BE2 applies to D23 to D16 BE3 applies to D31 to D24 When any one of the BE pin goes low, data bytes are transferred to or from the microprocessor from the corresponding data lines When all are low then complete 32 bit data is transferred between microprocessor and memory in one7 machine cycle
09-10-2012
Pin configuration cont. BS16(bus size 16): If logic 0/1 is applied on BS16 pin, then it indicates the size of the external data bus is of 16 bits/32 bits respectively, so the µp has to use 16/32 data pins correspondingly. If bus size is of 16 bits then 32 bit data will be transferred in two machine cycles. READY: If the ready input is 0, then µp performs normal operation or normal machine cycle without any wait state. If the ready i/p is 1,then the µp will introduce wait state in machine cycle. It is used along with slow devices. BY UBAID SAUDAGAR
8
09-10-2012
Pin configuration cont. PEREQ(Processor extension request): If the coprocessor is connected in the system, then the data transfer between the coprocessor and memory is performed by the main processor 80386. Whenever the 80387 has to perform data transfer then it will give logic 1 on PEREQ pin of the 80386. The physical address of memory location is generated by 80386. This address and read/write control signals is transferred by 80386, but the data transfer is performed between coprocessor and memory. BY UBAID SAUDAGAR
9
09-10-2012
Pin configuration cont.
BY UBAID SAUDAGAR
BUSY: If the instruction wait is given to the microprocessor, then the µp will check the BUSY pin. If the BUSY input is 0, then the µp will remain in the wait state. When the BUSY input becomes 1, then the µp will exit from the wait state and will execute next instruction in sequence. ERROR: When the coprocessor performs any operation and if error is obtained in the result, the coprocessor will give logic 0 on the ERROR pin of the µp. So the µp is interrupted on dedicated interrupt INT16. The ISR of the INT16 is used to check the error flags of the coprocessor and display the message on the screen.10
09-10-2012
Pin configuration cont. HOLD AND HLDA: HOLD pin indicates that another bus master is requesting a local bus. It acknowledges it by making HLDA high. These two are generally used by DMA controller. It takes the charge over the system bus for DMA operation. HOLD signal is activated to inform the µp that it want’s the charge of the bus. When the µp receives the HOLD request it will issue HLDA as an acknowledgement. When the HOLD line becomes low, HLDA also becomes low and µp gets back the control over the system bus BY UBAID SAUDAGAR
11
09-10-2012
BY UBAID SAUDAGAR
12
09-10-2012
Pin configuration cont. W/R(write/read): When the µp writes the data into the memory or o/p device then it gives W/R = 1. When the µp reads data from memory or i/p device, then it gives W/R = 0. D/C(data / control): When data transfer operation is performed between µp and memory, or µp and the io device µp makes this signal go high. When the µp performs control operations like opcode fetch, giving INTA signal then µp makes this signal go low. BY UBAID SAUDAGAR
13
09-10-2012
Pin configuration cont. M/IO(memory/input-output): When the data transfer is performed between µp and memory then the µp gives high signal on this pin. When the data transfer takes place between µp and io device then µp gives a low signal on this pin.
BY UBAID SAUDAGAR
14
09-10-2012
Pin configuration cont. LOCK: it is a prefix, when it is low it prevents other processors from gaining access the system bus. This signal is activated by the LOCK instruction and remains active till this instruction is carried out. The o/p of this pin is applied to ic8289, which informs other processors that the system bus is going to remain LOCK with 80386. BY UBAID SAUDAGAR
15
09-10-2012
Pin configuration cont.
BY UBAID SAUDAGAR
ADS(address data strobe): µp has to transfer valid memory or i/o address on address pins, then to latch this address in the external latch, µp gives logic 0 on ADS pin. NA(next address): When the bus controller gives logic 0 on the NA pin, then the µp has to transfer the address of the next machine cycle, even if the current machine cycle is not completed. This is called as address pipelining and it increases the speed of 16 operation.
09-10-2012
Memory System of 80386DX
BY UBAID SAUDAGAR
17
09-10-2012
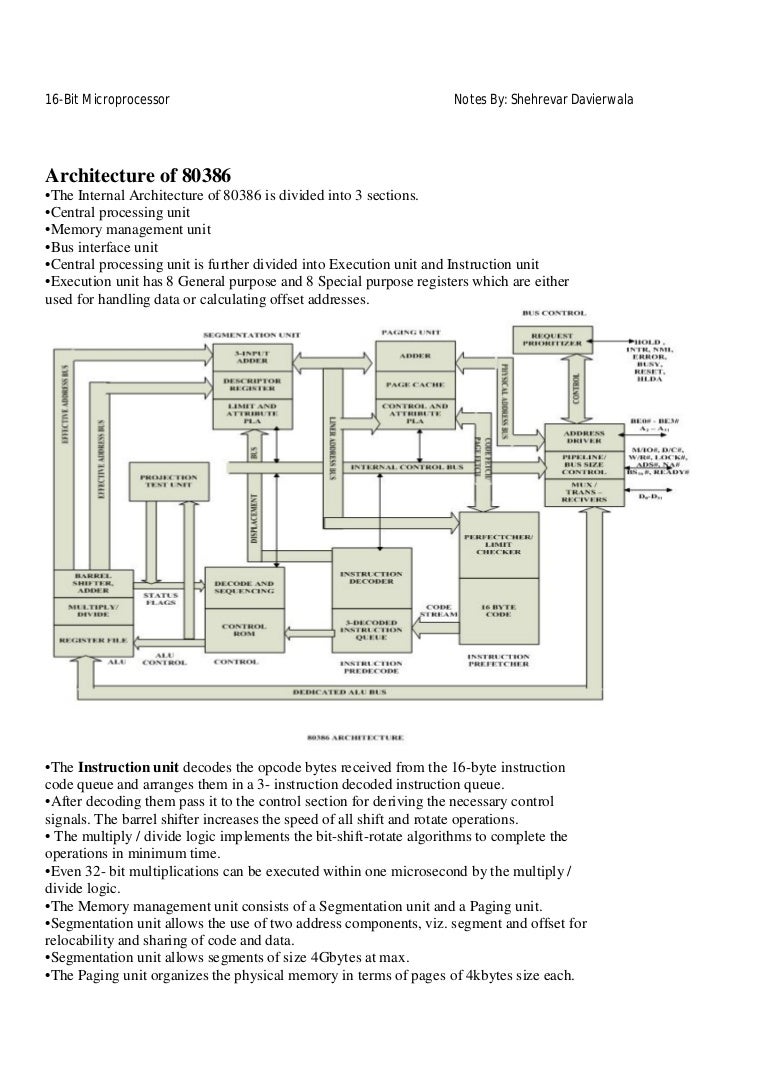
Architecture of 80386
BY UBAID SAUDAGAR
18
09-10-2012
Architecture of 80386 The 80386DX µp is available in a 132 pin array. It can operate in 16/20/25/33/ MHz frequencies If operating frequency is 33 MHz, then we have to apply double frequency i.e. 66 MHz's. The internal block diagram Is divided into six units
BY UBAID SAUDAGAR
19
09-10-2012
Bus interface unit It is used to transfer 32 bit address, data and control signals on system bus. In other words to interface with outside world BIU is used. If data transfer takes place between memory and co – processor, then address and control signals are transferred by BIU of 80386. The µp consist of 32 data pins, but can be used in systems as 16/32 bit. This information is indicated on BS16 pin. BIU also performs address pipelining, that is the address of next machine cycle is transferred on the address pins even if the current machine cycle is not completed. BY UBAID SAUDAGAR
20
09-10-2012
Code prefetch unit This unit will prefetch the instruction code and it is stored in the instruction queue which consists of 16, 8 bit registers.
BY UBAID SAUDAGAR
21
09-10-2012
Decode unit Prefetch unit will transfer instruction code to decode unit. This decode unit will pre decode 3 bytes of instruction codes and it is stored in the decoded instruction queue.
BY UBAID SAUDAGAR
22
09-10-2012
Execution unit It will execute decoded instruction to perform different arithmetic, logical, data transfer operations. It consist of different registers, flags, ALU and barrel shifter. The barrel shifter can be used to shift data by multiple bits in one clock cycle. So time required to execute rotate/shift/multiplication/division is reduced.
BY UBAID SAUDAGAR
23
09-10-2012
Segment unit It consists of segment registers and segment invisible cache register. In real mode segment registers are used to store the base address of memory. In protected mode segment registers are used to point the descriptors which contains information about memory, i.e. base address, limits and access rights. This information is transferred by µp to the segment invisible cache register.
BY UBAID SAUDAGAR
24
09-10-2012
Paging unit If the paging unit is enabled, then the 32 bit linear address generated in protected mode is translated using 2 level paging into 32 bit physical address. If paging unit is disabled, then 32 bit linear address is transferred as 32 bit physical address.
BY UBAID SAUDAGAR
25
09-10-2012
Register organization of 80386 80386 registers are categorized as follows: 1. General purpose registers 2. Instruction pointer and flags 3. Segment registers 4. System address registers 5. Control register 6. Debug register 7. Test register BY UBAID SAUDAGAR
26
09-10-2012
General purpose registers
BY UBAID SAUDAGAR
27
09-10-2012
General purpose registers
BY UBAID SAUDAGAR
The 8 general purpose registers of 32 bit hold data or address. A 32 - bit register known as an extended register, is represented by the register name with prefix E. Example : A 32 bit register corresponding to AX is EAX, similarly BX is EBX etc. The least significant 16 bits of the registers can be accessed separately. This is done by using the names AX, BX, CX, DX, SI, DI, BP and SP. The upper 16 bits are neither used nor changed. The lower and the higher bytes of general purpose registers i.e. AH,AL,BH,BL,CH,CL,DH,DL can also be accessed separately hence 28 providing more flexibility.
09-10-2012
Segment registers
BY UBAID SAUDAGAR
29
09-10-2012
Segment Registers Six segment registers hold the base address(in real mode) or segment selector values(in protected mode). The ES,GS,FS and DS all are generally used as data segments
BY UBAID SAUDAGAR
30
09-10-2012
Instruction pointer and flag register
BY UBAID SAUDAGAR
31
09-10-2012
Instruction pointer The instruction pointer is a 32 bit register named EIP It holds the offset of the next instruction which is to be executed The offset is always relative to the base address of Code segment(CS) The lower 16 bits are called as IP
BY UBAID SAUDAGAR
32
09-10-2012
Flag register
BY UBAID SAUDAGAR
33
09-10-2012
Carry flag
BY UBAID SAUDAGAR
34
09-10-2012
Auxiliary carry flag
BY UBAID SAUDAGAR
35
09-10-2012
Parity flag
BY UBAID SAUDAGAR
36
09-10-2012
Zero flag
BY UBAID SAUDAGAR
37
09-10-2012
Sign Flag
BY UBAID SAUDAGAR
38
09-10-2012
Overflow flag Bit 11 During the addition of two numbers, if their result exceeds the limit i.e. goes out of range, overflow flag is set.
BY UBAID SAUDAGAR
39
09-10-2012
Interrupt flag
BY UBAID SAUDAGAR
40
09-10-2012
Trap Flag
BY UBAID SAUDAGAR
41
09-10-2012
Direction flag
BY UBAID SAUDAGAR
42
09-10-2012
I/O privilege level
BY UBAID SAUDAGAR
43
09-10-2012
Nested task
BY UBAID SAUDAGAR
44
09-10-2012
Virtual 8086 mode Bit 17 This bit provides virtual 8086 mode within protected mode. When this bit is set while 80386 is in protected mode, the 80386 will switch to 8086 operations. It can be set only in the protected mode
BY UBAID SAUDAGAR
45
09-10-2012
Resume flag Bit 16 When RF is set, it causes any debug fault to be ignored on the next instruction. It is then automatically cleared on successful completion of every instruction (no fault is signaled).
BY UBAID SAUDAGAR
46
09-10-2012
Use of segment registers in protected mode The figure on pg. 48 shows that the segment register is used as selector in protected mode. The leftmost 13 bit index is a descriptor number The TI bit selects either local (TI = 1) or global (TI = 0) descriptor table, the RPL bits indicates the requested privilege level. Whenever the new selector number is loaded into one of the segment registers, the 80386 µp accesses one of the descriptor tables and automatically loads the descriptor into the segment invisible cache register. RPL = 00 (highest) RPL = 11 (lowest) BY UBAID SAUDAGAR
47
09-10-2012
Use of segment registers in protected mode
BY UBAID SAUDAGAR
48
09-10-2012
Addressing modes of 80386
REAL MODE: Real-address mode (often called just 'real mode') is the mode of the processor immediately after RESET. In real mode the 80386 appears to programmers as a fast 8086.
BY UBAID SAUDAGAR
49
09-10-2012
Addressing modes of 80386
PROTECTED MODE: Protected mode is the natural 32-bit environment of the 80386 processor. In this mode all instructions and features OF 80386 are available for utilization.
BY UBAID SAUDAGAR
50
09-10-2012
Addressing modes of 80386
VIRTUAL MODE: Virtual 8086 mode (also called V86 mode) is a dynamic mode in the sense that the processor can switch repeatedly and rapidly between V86 mode and protected mode. The CPU enters V86 mode from protected mode to execute an 8086 program, then leaves V86 mode and enters protected mode to continue executing a native 80386 program.
BY UBAID SAUDAGAR
51
09-10-2012
PROTECTED MODE
In the protected-mode, memory larger than 1 MB can be accessed. Note: Each descriptor corresponds to a segment with a maximum size of 4 GB or 232 bytes In addition, segments can be of variable size. In protected mode, the base : offset logical memory addressing scheme (which is used in real mode) is changed. In protected mode the segment register is used as selector that selects a descriptor from a descriptor table. The selector, selects one of 8192 descriptors from one of two tables of descriptors (stored in memory): the global and local descriptor tables. The descriptor describes the memory segment's location, length, and access rights. Each descriptor is 8 bytes long
BY UBAID SAUDAGAR
52
09-10-2012
PROTECTED MODE The 8192 descriptor table requires 8 * 8192 = 64K bytes of memory.
BY UBAID SAUDAGAR
53
09-10-2012
PROTECTED MODE The main parts of a descriptor are: Base (B31 – B0): indicates the starting location (base address) of the memory segment. Limit (L19 – L0): This defines the segment size. Since this field is 20 bits, the segment size varies upto 1M bytes. However, if the G bit (granularity bit) is set, the value of the limit is multiplied by 4K bytes (i.e., appended with FFFH). In this case, the segment size could be anywhere between 4K and 4G bytes.
BY UBAID SAUDAGAR
54
09-10-2012
PROTECTED MODE Example, Base = Start = 1000 0000h FFF = 1111 1111 1111 Limit = 001FFh and G = 0 appended at the end So, End = Base + Limit = 10000000h + 001FFh = 100001FFh Segment Size = 512 bytes Base = Start = 1000 0000h Limit = 001FFh and G = 1 So, End = Base + Limit * 4K = 10000000h + 001FF FFFh = 101FFFFFh Segment Size = 2M bytes BY UBAID SAUDAGAR
55
09-10-2012
Granular bit is 0
Offset address is 32 bits which varies from 000 00000 000 FFFFF
Since the descriptor contains limit of 20 bits with which the maximum size is 1 Mbyte 1 Descriptor
Question arises why blocks of 1 Mbyte? 1 Mbyte 1 Mbyte
This is the base address which is varying BY UBAID SAUDAGAR
000 00000 001 00000 002 00000 FFF 00000 With the help of base address different blocks are selected
1 Mbyte 1 Mbyte -
Total 4k blocks of 1 Mbyte associated with 1 descriptor
1 Mbyte 4 Gb memory associated with each56descriptor
Limit is multiplied by 4k,therefore now offset address which was varying as: Now is multiplied by 4k i.e. 4k x 1 Mb = 4 Gb Now offset varies from 0000 0000 09-10-2012 FFFF FFFF
PROTECTED MODE AV bit: is used by some operating systems to indicate that the segment is available (AV = 1) or not available (AV = 0). D bit: If D = 0, the instructions are 16-bit instructions, compatible with the 808680286 microprocessors. This means that the instructions use 16-bit offset addresses and 16-bit registers by default. If D = 1, the instructions are 32-bits by default. Access rights byte: allows complete control over the segment by defining the privilege level and other information about the segment. BY UBAID SAUDAGAR
57
09-10-2012
Address calculation in protected mode In protected mode the address is formed in such a way that the selector (16 bit segment register) selects one of the many descriptors from the descriptor table. The descriptor contains base address of the segment and the limit (which defines the maximum size of segment). Base address is of 32 bits and limit is of 20 bits (therefore the maximum size of the segment is 1Mbyte) Now the linear address is formed by adding the 32 bit offset with 32 bit base address to get 32 bit linear address. BY UBAID SAUDAGAR
58
09-10-2012
Descriptor contains base address, limit and access rights
32 bit offset
16 bit selector
Selects one of the many descriptors
0
0H
1
8H
2
10h
3
18h
32 bit base address
+
. . . 8191
BY UBAID SAUDAGAR
32 bit linear address
fff8h
Global or Local descriptor table
59
= Physical address, since paging is not enabled
09-10-2012
Address calculation in protected mode
Offset is of 32 bits therefore the maximum size of the segment possible is 4 Gb. But limit size is 20 bits and which indicates that maximum segment size is of 1 Mbyte. In above case we notice that the granular bit in the descriptor is 0. Due to which the offset gets added to base address but the upper 12 bits of offset are all 0’s.
BY UBAID SAUDAGAR
60
09-10-2012
Paging mechanism The segmentation scheme may divide the physical memory into variable size segments but the paging divides the memory into fixed size pages.
The advantage of the paging scheme is that the complete segment of a task need not be in the physical memory at any time. Only a few pages of the segments, which are required currently for the execution need to available in the physical memory. Thus the memory requirement of the task is reduced, therefore remaining memory is used for other tasks. Whenever the other pages of the task are required for execution, they may be fetched from the secondary storage. The previous pages which are executed need not be available in the memory. BY UBAID SAUDAGAR
61
09-10-2012
Paging Mechanism A key advantage to memory paging is that memory allocated to a program does not have to be contiguous, and because of that, there is very little internal fragmentation. Example: Show memory page allocation for the following sequence: Program A requests 3 pages of memory. Program C requests 2 pages of memory. Program D requests 2 pages of memory. Program C terminates, leaving 2 empty pages. Program B requests 3 pages of memory, and it is allocated the 2 empty pages that program C left, plus an additional page after program D. BY UBAID SAUDAGAR
62
09-10-2012
Paging Mechanism
BY UBAID SAUDAGAR
63
09-10-2012
Address calculation when paging is enabled The 32-bit linear address generated by the segmentation unit can be optionally fed into the paging unit to undergo a second address manipulation process.
BY UBAID SAUDAGAR
64
09-10-2012
Descriptor contains base address, limit and access rights
32 bit offset
16 bit selector
Selects one of the many descriptors
0
0H
1
8H
2
10h
3
18h
32 bit base address
+
. .
32 bit linear address
. 8191 BY Ubaid by UBAIDSaudagar SAUDAGAR
fff8h
Global or Local descriptor table
65
Goes to paging unit
09-10-2012
Address calculation when paging is enabled In the above figure we notice that, the linear address is formed by combining the base address and the offset address. This is actually the physical address in case of segmentation which is used to access the segments. But in case of paging this linear address is applied to paging unit and then physical address is formed which accesses the pages. Lets see how physical address is formed on pg. 67
BY UBAID SAUDAGAR
66
09-10-2012
(Upper 10 bits) Offset within page directory
+ Page directory of 4 Kb 4 bytes
+
4 bytes
(12 bits) offset within pages
Pages
-
Base address
Linear address
4 bytes Base address
4 bytes
+
4 kb 4 kb
4 bytes -
(next 10 bits) offset within page tables Page tables of 4 Kb each
4 bytes
-
1024 entries, each entry is base address of page Each table table has 1024 entries, each UBAID SAUDAGAR entry points CR3BY gives the base address to a page
1024 page tables
4 bytes -
-
4 kb
4 bytes 4 bytes
Total number of pages = 1024 * 1024 =- 1048576 = 1M -
67
Offset address varies within a page = 0000 0000 0000 = 000 1 1 1 1 1 1 1 1 1 1 1 1 = FFF09-10-2012
Virtual address 801C3400H 10 0000 0000 (200H)
200h
01 1100 0011 (1C3H)
0100 0000 0000 (400H)
This physical address is used to access a page
000E4000h
00028000h
Physical address =
+ 00028400h
Base address BY UBAID SAUDAGAR
68
09-10-2012
Address calculation when paging is enabled A close examination of the paging process reveals that the processor breaks the linear address into three components before turning it into a physical one.
The top 10 bits of the linear address are used by the processor to index or point the page directory table. The next 10 bits of the linear address serve as an index into the corresponding page table. By adding the page table entry value that is actually the base address to the page and the offset which comes from the last 12 bits of linear address we can locate the requested physical address and send it to its address bus and access a page. BY UBAID SAUDAGAR
69
09-10-2012
Address calculation when paging is enabled The linear address obtained by combining the base address (obtained from descriptor) and offset address is split up into three parts by the MMU. The upper 10 bits are used to select the entries in the page directory. Page directory : The page directory contains 1024 page directory entries, each of which is 4 bytes (32 bits). This means the page directory is 4 K bytes long. There is only one page directory in memory and its base address is contained in CR3. With the help of base address page directory is selected and with the help of offset the entries in the page directory is selected. Imp: The total entries in the page directory are 1024. Therefore to access these entries we require 10 addressing bits which we get from the upper 10 bits of linear address. BY UBAID SAUDAGAR
70
09-10-2012
Address calculation when paging is enabled Therefore the 10 bits(offset) will vary as: 00 0000 0000 = 000 (hex) = 0 1 1 1 1 1 1 1 1 1 1 = 3FF (hex) = 1023 (decimal) Now each address will select an entry in the page directory table. But, each entry is of 4 bytes therefore total number no. of memory locations are: 1024 * 4 = 4096, therefore to address 4096 locations 12 bits are required hence the MMU appends two bits at the end and their value are always 00 Now the offset will vary as: 0000 0000 00 00 = 000 (hex) = 0th location 0000 0000 01 00 = 004 (hex) = 4th location 0000 0000 10 00 = 008 (hex) = 8th location First 10 bits 1 1 1 1 1 1 1 1 1 1 00 = FFC (hex) = 1024th location BY UBAID SAUDAGAR
71
09-10-2012
Address calculation when paging is enabled The next 10 bits are used to select the entries within the page tables. Page table: Page directory has 1024 entries and each entry selects a page table. Each page table contains 1024 page table entries, each of which is 4 bytes (32 bits). This means that each page table is 4 K bytes long. As such there are 1024 page tables and each table of 4Kb. Each page table entry is actually the base address to a page in the page frame. Therefore number of pages accessed or addressed are 1024 (1 page table entries) * 1024 (number of page tables) = 1048576 = 1 Mb pages. Note: The number of bits available as offset to move within the page table are 10 i.e. same as page directory, hence addressing is same as explained previously. BY UBAID SAUDAGAR
72
09-10-2012
Address calculation when paging is enabled The next 12 bits are used as offset to move within the pages of 4Kb. It is important to notice that 10 bits are used to address entries in the page directory(even though PD requires 4Kb of memory), 10bits are used to address entries in the page table (even though PT requires 4Kb of memory), 12 bits are required as offset to move within a page (even though page size is of 4Kb). This is because MMU appends 00 at the end of 10 bits hence it moves within a PD and PT and addresses 4kb of memory and only the entries which are 1024 for which only 10 bits are required. BY UBAID SAUDAGAR
73
09-10-2012
Address calculation when paging is enabled
Page: Each page table entry points to the starting physical address of a page in memory (i.e., the physical page number). In other words each entry in the page table acts as base address to a page and the 12 bits from the linear address acts as offset address. Number of pages accessed or addressed are 1024 (1 page table entries) * 1024 (number of page tables) = 1048576 = 1 Mb pages. 1M pages * 4K (size of each page) = 4Gb space = size of page frame
BY UBAID SAUDAGAR
74
09-10-2012
Note: The memory-management unit (MMU) within the 80386 is similar to the MMU inside the 80286, except that the 80386 contains a paging unit not found in the 80286. The MMU performs the task of converting linear addresses, as they appear as outputs from a program, into physical addresses that access a physical memory location located anywhere within the memory system.
BY UBAID SAUDAGAR
75
09-10-2012
Translation look aside buffer A translation look aside buffer (TLB) is a cache that memory management hardware uses to improve virtual address translation speed.
Since the page directory and page tables are of 4kb, it would be very inefficient to have to access them every time an address requires translation since two memory reads are needed to read the entries from each table. This requires n number of clock cycles. To improve performance, a 32-entry page table cache is provided which stores the 32 recently accessed page table entries. Whenever a linear address is to be converted to physical address, it is first checked to see, whether it corresponds to any of the page table cache entries. This page table cache is called as translation look-aside buffer (TLB) that automatically translate the upper 20 bits of the virtual address into upper 20 physical address bits. BY UBAID SAUDAGAR
76
09-10-2012
Translation look aside buffer 10 bits
10bits
12 bits (offset)
20 bits Valid virtual upper 20 bits physical upper 20 bits 0
TLB
0 0
+
1
Physical address
0 0 0 BY UBAID SAUDAGAR
0
77
09-10-2012
Translation look aside buffer Whenever a linear address is formed, it gets converted to physical address through 2 level paging (i.e. PD and PT). The resent addresses (linear and physical) are stored in the TLB. Thus from the above figure we see that the Translation look aside buffer (TLB) contains upper 20 bits of virtual address (linear address) as well as upper 20 bits of physical address. Whenever any page is to be accessed, this linear address needs to be converted again and again to physical address through 2 level paging. To avoid this and to access the most resent pages or to access some pages again and again quickly we use TLB. The linear address (virtual address) is stored in TLB along with its corresponding physical address, if the required linear address is available then it’s corresponding physical address is retrieved and combined with the offset to access the page. This happens in a single clock cycle. BY UBAID SAUDAGAR
78
09-10-2012
Control Registers
Figure below shows the format of the 80386 control registers CR0, CR2, and CR3. CR0 contains system control flags, which control or indicate conditions that apply to the system as a whole, not to an individual task.
BY UBAID SAUDAGAR
79
09-10-2012
Control registers 16 MSB P G
16 LSB
0---------------------------------------------------------------------------0 0-------------------------------------------------------------------------0 E T E M P T S M P E CR0 INTEL RESERVED
CR1
PAGE FAULT LINEAR ADDRESS
PAGE DIRECTORY BASE ADDRESS
BY UBAID SAUDAGAR
CR2
0000 0000 0000
80
CR3
09-10-2012
Control Registers Control Register (CR0): Machine Control Register As shown in figure, control register CR0 contains six defined bits for control and status purposes. The low order 16 bits of CR0 are also known as machine status word(MSW), for compatibility with 80286 protected mode. The defined CR0 bits are described below: BY UBAID SAUDAGAR
81
09-10-2012
Cont. PG (Paging, bit 31): If paging bit is 1/0, then paging is enabled/disabled from the on-chip paging unit. ET (Extension Coprocessor,bit4): If 0/1, then it indicates that the microprocessor 80386 is connected with the co-processor 80287/80387. The 80386 is designed to operate with either an 80287 or 80387 math coprocessor. The ET bit of CR0 indicates which type of coprocessor is present. ET is set automatically by the 80386 after RESET If ET is set, the 80386 uses the 32-bit protocol of the 80387; if reset, the 80386 uses the 16-bit protocol of the 80287. BY UBAID SAUDAGAR
82
09-10-2012
Cont.
TS(Task switch, bit 3): TS is automatically set whenever a task switch operation is performed. If TS = 1, then the µp will execute more than one program. If TS = 0, then µp will not performing task switching, i.e. not going to another program without executing first program. EM (Emulate Co-processor, bit 2): If EM = 1, then whenever Coprocessor instructions comes in the program then µp executes INT7 (exception 7). The ISR of INT7 is used to execute the operation of the co processor instructions using software. It will take nearly 100 times more time compared to the time required by the co processor. If EM = 0, then it allows the co processor opcodes to be actually executed on an actually 80387DX co processor (this is the default case after reset). BY UBAID SAUDAGAR
83
09-10-2012
Cont. MP (Monitor Processor extension (co - processor), bit 1 ): If MP = 1/0, then it indicates that co processor is present/not present respectively. When the co processor is connected to 80386, then there is no meaning of the EM bit, i.e. when MP = 1, then there is no use of EM. PE (Protection enable, bit 0): If PE = 1, then the 80386 gets defined from real mode to protected mode. If PE = 0, then 80386 again operates in real mode. BY UBAID SAUDAGAR
84
09-10-2012
Cont. Control register (CR1) : Intel Reserved It is reserved by Intel for used in future microprocessor IC’s Control register (CR2) : Page fault linear address If the paging unit is enabled, but if there is any fault in paging unit, then 32 bit linear address is saved in register CR2 and the µp executes exception (dedicated interrupt, INT14) to display the error message.
BY UBAID SAUDAGAR
85
09-10-2012
Cont. Control Register (CR3): Page directory base address A directory table points to the page table and page table points to page frame. Directory table is pointed by CR3 (i.e. the base address or starting address or root address of directory table is present in CR3) Note that this address locates the page directory at any 4K boundary in the memory system because it is appended internally with 000h.
BY UBAID SAUDAGAR
86
09-10-2012
Invisible register Every memory segment is associated with a descriptor. When other memory segment is to be selected, i.e. the next memory segment, the base address of previous one is automatically stored in invisible register (IR). The invisible register is operated by the microprocessor, i.e. the IR is unused by the programmer.
BY UBAID SAUDAGAR
87
09-10-2012
System address registers GDTR = Global Descriptor Table Register
LDTR = Local Descriptor Table Register TR = Task Register
BY UBAID SAUDAGAR
88
09-10-2012
Physical memory
GDTR GDTR
Since limit has 16 bits, size of GDT is 64kb
Descriptor 8191
Descriptor 8190 Descriptor 8189
Length of the GDT
47
16 15 Base address
0
-
Limit
Descriptor 1 BA
Descriptor 0
80386 microprocessor
BY UBAID SAUDAGAR
89
09-10-2012
GDTR GDT consist of descriptors which are available to almost all the task in the system The contents of the global descriptor table register define a table in the 80386DX's physical memory address space called the Global Descriptor Table (GDT). GDTR is a 48-bit register that is located inside the 80386DX. The lower two bytes of this register, which are identified as LIMIT, specify the size in byte of the GDT. Since LIMIT has 16 bits, the GDT can be up to 65,536 bytes long. The upper four bytes of the GDTR, which are labelled BASE, locate the beginning of the GDT in physical memory. This 32-bit base address allows the table to be positioned anywhere in the 80386DX's address space BY UBAID SAUDAGAR
90
09-10-2012
LDTR
Physical memory Descriptor 8191 -
15 LDTR
Descriptor n
0
GDT
-
Selector no. n
Descriptor 0 LDTR invisible or cache register 47 Base address
16 15
0
Descriptor 8191
Limit
Descriptor 1
LDT
Base address BY UBAID SAUDAGAR
91
Descriptor 0 09-10-2012
LDTR Firstly the main difference between GDT and LDT is that, GDT consist of descriptors which are global and LDT consist of those descriptors which are associated to a particular task.
Now the question arises how this LDT gets created? LDTR is a 16 bit selector which selects one of the descriptors from the GDT, from there it gets the base address and limit. In other words LDTR is a 16 bit selector which points to a LDT descriptor in the GDT. This 32 bit base address and 16 bit limit value are stored in a LDTR invisible register also called as cache register. Now this base address is the starting location of LDT in physical memory and limit defines the maximum size of the LDT. BY UBAID SAUDAGAR
92
09-10-2012
Task register (TR) The task register is one of the key elements in the protected mode task switching mechanism of the 80386DX microprocessor. This register holds a 16-bit index value called a selector. TR is used to locate a descriptor in the global descriptor table The initial selector must be loaded into TR under software control. This starts the initial task. After this is done, the selector is changed automatically whenever the 80386DX executes an instruction that performs a task switching. BY UBAID SAUDAGAR
93
09-10-2012
Debug registers 31
0 Breakpoint address 0
𝐷𝑅0
Breakpoint address 1
𝐷𝑅1
Breakpoint address 2
𝐷𝑅2
Breakpoint address 3
𝐷𝑅3
Intel reserved
𝐷𝑅4
Intel reserved Breakpoint status BY UBAID SAUDAGAR
94 control Breakpoint
𝐷𝑅5 𝐷𝑅6 09-10-2012
𝐷𝑅7
Debug registers
There are in all six debug registers which are accessible to the programmer and on chip support for debugging.
Debug registers 𝐷𝑅0 - 𝐷𝑅3 specify the four linear breakpoints. In other words, the addresses (32 bit address)where we place a breakpoint, that address is stored in these 4 registers. These addresses are constantly compared with the address generated by the program. If a match occurs then 80386 will cause type 1 interrupt (TRAP) indicating to stop executing in free run mode. Debug control register 𝐷𝑅7 is used to set the breakpoints. Debug status register 𝐷𝑅6 is used to check the current status of the breakpoints. BY UBAID SAUDAGAR
95
09-10-2012
Test registers
31
BY UBAID SAUDAGAR
0 Test command register
𝑇𝑅6
Test data register
𝑇𝑅7
96
09-10-2012
Test registers The Intel 386DX provides a mechanism for testing the TLB if desired. This particular mechanism is unique to Intel386 DX. Two test registers are used for testing mechanism viz. Test command register (𝑇𝑅6 ) and Test Data register (𝑇𝑅7 ). There are two TLB testing operations: 1. Write entries into the TLB 2. Perform TLB lookups When we need to test the TLB, paging must be turned off i.e. (PG = 0 in 𝐶𝑅0 ) to enable the TLB testing hardware and avoid interference with the test data being written to the TLB. BY UBAID SAUDAGAR
97
09-10-2012
Virtual 8086 mode of 80386 microprocessor In the real mode, µp works as a fast 8086. In the protected mode all the features of 80386 are available. But to come back to real mode, the only way was to reset the µp. Thus, the virtual 8086 mode of operation of 80386 offers an advantage of executing 8086 programs while in protected mode. Whenever we boot the µp, it is by default in the real mode. To go the protected mode the PE bit in CR0 is set to 1. Now we are in the protected mode, generally to go back to real mode the only way was to reset the µp, but now due to V8086 mode we can switch to real mode without reset. BY UBAID SAUDAGAR
98
09-10-2012
Virtual 8086 mode of 80386 microprocessor Virtual 8086 mode is entered by changing the VM bit in the EFLAG register to a logic 1. This mode is entered via an IRET instruction if the privilege level is 00. This bit cannot be set in any other manner. Therefore VM bit tells us that whether we are using 8086 instructions or 80386 instructions. The address forming mechanism in virtual 8086 mode is identical to that of 8086. The 80386 allows the operating system to specify which programs use 8086 style address mechanism and which programs use protected mode addressing. The virtual 8086 mode executes all the programs at privilege level 3 (the least privilege). BY UBAID SAUDAGAR
99
09-10-2012
Virtual 8086 mode of 80386 microprocessor TaskA of 80386
µp TaskC of 80386
TaskB of 8086
BY UBAID SAUDAGAR
100
09-10-2012
Virtual 8086 mode of 80386 microprocessor Consider the above example:
To execute task A we need to enter to enter in the protected mode as it is a 80386 program. Now when the processor switches to task B to execute 8086 program, programmer executes IRET instruction at privilege level 00 which sets the VM bit in the EFLAG register. BY UBAID SAUDAGAR
101
09-10-2012
Difference between 80286 and 80386 80286
80386
16 bit microprocessor Accessible memory: Physical memory = 16Mb Virtual memory = 1 Gb Address bus = 24 bits Data bus = 16 bits Paging mechanism not supported Control registers and test registers not present On chip debug registers not present To move from protected mode to real mode µp needs to be reset. BY UBAID SAUDAGAR
102
32 bit microprocessor Accessible memory: Physical memory = 4 Gb Virtual memory = 64 Tb Address bus = 32 bits Data bus = 32 bits Supports 2 level paging mechanism Control registers and test registers present On chip debug registers To move from protected mode to real mode VM bit in the EFLAG must be set i.e. VM =1 09-10-2012
Data types supported by 80386 Unsigned integer number
Byte
Word
Signed integer number
Unpacked BCD number
ASCII numbers or codes
Real numbers
Byte
9 in packed BCD is 1001
9 in unpacked BCD is 0000 1001
Short real number = 32 bit
Word
87 in packed BCD is 1000 0111
87 in packed BCD is 0000 1000 0000 0111
Long real number = 64 bit
Dword
Dword
Qword
Qword
BY UBAID SAUDAGAR
Packed BCD number
Temporary real number = 80 bit
103
09-10-2012
Signal Descriptions of 80386. W/R#:The write / read output distinguishes the write and read cycles from one another. D/C#:This data / control output pin distinguishes between a data transfer cycle from a machine control cycle like interrupt acknowledge. M/IO#:This output pin differentiates between the memory and I/O cycles. 80386 Datasheet, 80386 PDF, 80386 Data sheet, 80386 manual, 80386 pdf, 80386, datenblatt, Electronics 80386, alldatasheet, free, datasheet, Datasheets, data sheet.

Microprocessor History
Salient features 1. 2. 3. 4. 5.
BY UBAID SAUDAGAR
Flexible 32 bit microprocessor Address bus is of 32-bit Operating frequency of 20-33 MHz . Contains total 132 Pins. Intel’s first practical microprocessor to contain a 32-bit data bus and 32-bit memory address. 6. 16 byte prefetch queue 7. Very large address space a. 4 Gb of physical memory supported b. 64 Tb of virtual memory supported c. 4 Gb of maximum segment size 8. Integrated memory management unit 9. Object code compatible with all 8086 family microprocessors 10. High speed numeric support via 80387 11. Can operates in real, protected & virtual Mode 12. Introduced paging, virtual memory concept 13. Can operate at 11.4 MIPS. 14. Contains near about 2,75,000 Transistors.2
09-10-2012
Versions of 80386 Microprocessor
BY UBAID SAUDAGAR
(A) 80386 SX
(B) 80386 DX
(1). A.B. is of 32 Bit. (2). D.B. is of 32 Bit. (3). Total 132 Pins. (4). Can address upto 4GB of memory.
(1). A.B. is of 24 Bit. (2). D.B. is of 16 Bit. (3). Total 100 Pins. (4). Can address upto 16MB of memory. 3
09-10-2012
Pin configuration
BY UBAID SAUDAGAR
4
09-10-2012
Pin configuration cont.
BY UBAID SAUDAGAR
5
09-10-2012
Pin configuration cont. Data bus(D31 – D0): It consist of 32 data pins, therefore memory is connected in 4 banks(bank 0 – bank 3). So the 80386 can transfer 8/16/32 bit data in one machine cycle. Address bus(A31 –A2, BE3 – BE0): With the help of address lines, it is able to address 4GB of physical memory space from 00000000H to FFFFFFFFH. 4GB is connected as 4 banks of 1GB each. Therefore to address 1GB of memory, 30 address lines are required i.e. from A2-A31. BY UBAID SAUDAGAR
6
09-10-2012
Pin configuration cont.
BY UBAID SAUDAGAR
Lower two address pins A1 and A0 are internally decoded by 80386 to generate 4 bank enable signals(BE3 – BE0) BE0 applies to D7 to D0 BE1 applies to D15 to D8 BE2 applies to D23 to D16 BE3 applies to D31 to D24 When any one of the BE pin goes low, data bytes are transferred to or from the microprocessor from the corresponding data lines When all are low then complete 32 bit data is transferred between microprocessor and memory in one7 machine cycle
09-10-2012
Pin configuration cont. BS16(bus size 16): If logic 0/1 is applied on BS16 pin, then it indicates the size of the external data bus is of 16 bits/32 bits respectively, so the µp has to use 16/32 data pins correspondingly. If bus size is of 16 bits then 32 bit data will be transferred in two machine cycles. READY: If the ready input is 0, then µp performs normal operation or normal machine cycle without any wait state. If the ready i/p is 1,then the µp will introduce wait state in machine cycle. It is used along with slow devices. BY UBAID SAUDAGAR
8
09-10-2012
Pin configuration cont. PEREQ(Processor extension request): If the coprocessor is connected in the system, then the data transfer between the coprocessor and memory is performed by the main processor 80386. Whenever the 80387 has to perform data transfer then it will give logic 1 on PEREQ pin of the 80386. The physical address of memory location is generated by 80386. This address and read/write control signals is transferred by 80386, but the data transfer is performed between coprocessor and memory. BY UBAID SAUDAGAR
9
09-10-2012
Pin configuration cont.
BY UBAID SAUDAGAR
BUSY: If the instruction wait is given to the microprocessor, then the µp will check the BUSY pin. If the BUSY input is 0, then the µp will remain in the wait state. When the BUSY input becomes 1, then the µp will exit from the wait state and will execute next instruction in sequence. ERROR: When the coprocessor performs any operation and if error is obtained in the result, the coprocessor will give logic 0 on the ERROR pin of the µp. So the µp is interrupted on dedicated interrupt INT16. The ISR of the INT16 is used to check the error flags of the coprocessor and display the message on the screen.10
09-10-2012
Pin configuration cont. HOLD AND HLDA: HOLD pin indicates that another bus master is requesting a local bus. It acknowledges it by making HLDA high. These two are generally used by DMA controller. It takes the charge over the system bus for DMA operation. HOLD signal is activated to inform the µp that it want’s the charge of the bus. When the µp receives the HOLD request it will issue HLDA as an acknowledgement. When the HOLD line becomes low, HLDA also becomes low and µp gets back the control over the system bus BY UBAID SAUDAGAR
11
09-10-2012
BY UBAID SAUDAGAR
12
09-10-2012
Pin configuration cont. W/R(write/read): When the µp writes the data into the memory or o/p device then it gives W/R = 1. When the µp reads data from memory or i/p device, then it gives W/R = 0. D/C(data / control): When data transfer operation is performed between µp and memory, or µp and the io device µp makes this signal go high. When the µp performs control operations like opcode fetch, giving INTA signal then µp makes this signal go low. BY UBAID SAUDAGAR
13
09-10-2012
Pin configuration cont. M/IO(memory/input-output): When the data transfer is performed between µp and memory then the µp gives high signal on this pin. When the data transfer takes place between µp and io device then µp gives a low signal on this pin.
BY UBAID SAUDAGAR
14
09-10-2012
Pin configuration cont. LOCK: it is a prefix, when it is low it prevents other processors from gaining access the system bus. This signal is activated by the LOCK instruction and remains active till this instruction is carried out. The o/p of this pin is applied to ic8289, which informs other processors that the system bus is going to remain LOCK with 80386. BY UBAID SAUDAGAR
15
09-10-2012
Pin configuration cont.
BY UBAID SAUDAGAR
ADS(address data strobe): µp has to transfer valid memory or i/o address on address pins, then to latch this address in the external latch, µp gives logic 0 on ADS pin. NA(next address): When the bus controller gives logic 0 on the NA pin, then the µp has to transfer the address of the next machine cycle, even if the current machine cycle is not completed. This is called as address pipelining and it increases the speed of 16 operation.
09-10-2012
Memory System of 80386DX
BY UBAID SAUDAGAR
17
09-10-2012
Architecture of 80386
BY UBAID SAUDAGAR
18
09-10-2012
Architecture of 80386 The 80386DX µp is available in a 132 pin array. It can operate in 16/20/25/33/ MHz frequencies If operating frequency is 33 MHz, then we have to apply double frequency i.e. 66 MHz's. The internal block diagram Is divided into six units
BY UBAID SAUDAGAR
19
09-10-2012
Bus interface unit It is used to transfer 32 bit address, data and control signals on system bus. In other words to interface with outside world BIU is used. If data transfer takes place between memory and co – processor, then address and control signals are transferred by BIU of 80386. The µp consist of 32 data pins, but can be used in systems as 16/32 bit. This information is indicated on BS16 pin. BIU also performs address pipelining, that is the address of next machine cycle is transferred on the address pins even if the current machine cycle is not completed. BY UBAID SAUDAGAR
20
09-10-2012
Code prefetch unit This unit will prefetch the instruction code and it is stored in the instruction queue which consists of 16, 8 bit registers.
BY UBAID SAUDAGAR
21
09-10-2012
Decode unit Prefetch unit will transfer instruction code to decode unit. This decode unit will pre decode 3 bytes of instruction codes and it is stored in the decoded instruction queue.
BY UBAID SAUDAGAR
22
09-10-2012
Execution unit It will execute decoded instruction to perform different arithmetic, logical, data transfer operations. It consist of different registers, flags, ALU and barrel shifter. The barrel shifter can be used to shift data by multiple bits in one clock cycle. So time required to execute rotate/shift/multiplication/division is reduced.
BY UBAID SAUDAGAR
23
09-10-2012
Segment unit It consists of segment registers and segment invisible cache register. In real mode segment registers are used to store the base address of memory. In protected mode segment registers are used to point the descriptors which contains information about memory, i.e. base address, limits and access rights. This information is transferred by µp to the segment invisible cache register.
BY UBAID SAUDAGAR
24
09-10-2012
Paging unit If the paging unit is enabled, then the 32 bit linear address generated in protected mode is translated using 2 level paging into 32 bit physical address. If paging unit is disabled, then 32 bit linear address is transferred as 32 bit physical address.
BY UBAID SAUDAGAR
25
09-10-2012
Register organization of 80386 80386 registers are categorized as follows: 1. General purpose registers 2. Instruction pointer and flags 3. Segment registers 4. System address registers 5. Control register 6. Debug register 7. Test register BY UBAID SAUDAGAR
26
09-10-2012
General purpose registers
BY UBAID SAUDAGAR
27
09-10-2012
General purpose registers
BY UBAID SAUDAGAR
The 8 general purpose registers of 32 bit hold data or address. A 32 - bit register known as an extended register, is represented by the register name with prefix E. Example : A 32 bit register corresponding to AX is EAX, similarly BX is EBX etc. The least significant 16 bits of the registers can be accessed separately. This is done by using the names AX, BX, CX, DX, SI, DI, BP and SP. The upper 16 bits are neither used nor changed. The lower and the higher bytes of general purpose registers i.e. AH,AL,BH,BL,CH,CL,DH,DL can also be accessed separately hence 28 providing more flexibility.
09-10-2012
Segment registers
BY UBAID SAUDAGAR
29
09-10-2012
Segment Registers Six segment registers hold the base address(in real mode) or segment selector values(in protected mode). The ES,GS,FS and DS all are generally used as data segments
BY UBAID SAUDAGAR
30
09-10-2012
Instruction pointer and flag register
BY UBAID SAUDAGAR
31
09-10-2012
Instruction pointer The instruction pointer is a 32 bit register named EIP It holds the offset of the next instruction which is to be executed The offset is always relative to the base address of Code segment(CS) The lower 16 bits are called as IP
BY UBAID SAUDAGAR
32
09-10-2012
Flag register
BY UBAID SAUDAGAR
33
09-10-2012
Carry flag
BY UBAID SAUDAGAR
34
09-10-2012
Auxiliary carry flag
BY UBAID SAUDAGAR
35
09-10-2012
Parity flag
BY UBAID SAUDAGAR
36
09-10-2012
Zero flag
BY UBAID SAUDAGAR
37
09-10-2012
Sign Flag
BY UBAID SAUDAGAR
38
09-10-2012
Overflow flag Bit 11 During the addition of two numbers, if their result exceeds the limit i.e. goes out of range, overflow flag is set.
BY UBAID SAUDAGAR
39
09-10-2012
Interrupt flag
BY UBAID SAUDAGAR
40
09-10-2012
Trap Flag
BY UBAID SAUDAGAR
41
09-10-2012
Direction flag
BY UBAID SAUDAGAR
42
09-10-2012
I/O privilege level
BY UBAID SAUDAGAR
43
09-10-2012
Nested task
BY UBAID SAUDAGAR
44
09-10-2012
Virtual 8086 mode Bit 17 This bit provides virtual 8086 mode within protected mode. When this bit is set while 80386 is in protected mode, the 80386 will switch to 8086 operations. It can be set only in the protected mode
BY UBAID SAUDAGAR
45
09-10-2012
Resume flag Bit 16 When RF is set, it causes any debug fault to be ignored on the next instruction. It is then automatically cleared on successful completion of every instruction (no fault is signaled).
BY UBAID SAUDAGAR
46
09-10-2012
Use of segment registers in protected mode The figure on pg. 48 shows that the segment register is used as selector in protected mode. The leftmost 13 bit index is a descriptor number The TI bit selects either local (TI = 1) or global (TI = 0) descriptor table, the RPL bits indicates the requested privilege level. Whenever the new selector number is loaded into one of the segment registers, the 80386 µp accesses one of the descriptor tables and automatically loads the descriptor into the segment invisible cache register. RPL = 00 (highest) RPL = 11 (lowest) BY UBAID SAUDAGAR
47
09-10-2012
Use of segment registers in protected mode
BY UBAID SAUDAGAR
48
09-10-2012
Addressing modes of 80386
REAL MODE: Real-address mode (often called just 'real mode') is the mode of the processor immediately after RESET. In real mode the 80386 appears to programmers as a fast 8086.
BY UBAID SAUDAGAR
49
09-10-2012
Addressing modes of 80386
PROTECTED MODE: Protected mode is the natural 32-bit environment of the 80386 processor. In this mode all instructions and features OF 80386 are available for utilization.
BY UBAID SAUDAGAR
50
09-10-2012
Addressing modes of 80386
VIRTUAL MODE: Virtual 8086 mode (also called V86 mode) is a dynamic mode in the sense that the processor can switch repeatedly and rapidly between V86 mode and protected mode. The CPU enters V86 mode from protected mode to execute an 8086 program, then leaves V86 mode and enters protected mode to continue executing a native 80386 program.
BY UBAID SAUDAGAR
51
09-10-2012
PROTECTED MODE
In the protected-mode, memory larger than 1 MB can be accessed. Note: Each descriptor corresponds to a segment with a maximum size of 4 GB or 232 bytes In addition, segments can be of variable size. In protected mode, the base : offset logical memory addressing scheme (which is used in real mode) is changed. In protected mode the segment register is used as selector that selects a descriptor from a descriptor table. The selector, selects one of 8192 descriptors from one of two tables of descriptors (stored in memory): the global and local descriptor tables. The descriptor describes the memory segment's location, length, and access rights. Each descriptor is 8 bytes long
BY UBAID SAUDAGAR
52
09-10-2012
PROTECTED MODE The 8192 descriptor table requires 8 * 8192 = 64K bytes of memory.
BY UBAID SAUDAGAR
53
09-10-2012
PROTECTED MODE The main parts of a descriptor are: Base (B31 – B0): indicates the starting location (base address) of the memory segment. Limit (L19 – L0): This defines the segment size. Since this field is 20 bits, the segment size varies upto 1M bytes. However, if the G bit (granularity bit) is set, the value of the limit is multiplied by 4K bytes (i.e., appended with FFFH). In this case, the segment size could be anywhere between 4K and 4G bytes.
BY UBAID SAUDAGAR
54
09-10-2012
PROTECTED MODE Example, Base = Start = 1000 0000h FFF = 1111 1111 1111 Limit = 001FFh and G = 0 appended at the end So, End = Base + Limit = 10000000h + 001FFh = 100001FFh Segment Size = 512 bytes Base = Start = 1000 0000h Limit = 001FFh and G = 1 So, End = Base + Limit * 4K = 10000000h + 001FF FFFh = 101FFFFFh Segment Size = 2M bytes BY UBAID SAUDAGAR
55
09-10-2012
Granular bit is 0
Offset address is 32 bits which varies from 000 00000 000 FFFFF
Since the descriptor contains limit of 20 bits with which the maximum size is 1 Mbyte 1 Descriptor
Question arises why blocks of 1 Mbyte? 1 Mbyte 1 Mbyte
This is the base address which is varying BY UBAID SAUDAGAR
000 00000 001 00000 002 00000 FFF 00000 With the help of base address different blocks are selected
1 Mbyte 1 Mbyte -
Total 4k blocks of 1 Mbyte associated with 1 descriptor
1 Mbyte 4 Gb memory associated with each56descriptor
Limit is multiplied by 4k,therefore now offset address which was varying as: Now is multiplied by 4k i.e. 4k x 1 Mb = 4 Gb Now offset varies from 0000 0000 09-10-2012 FFFF FFFF
PROTECTED MODE AV bit: is used by some operating systems to indicate that the segment is available (AV = 1) or not available (AV = 0). D bit: If D = 0, the instructions are 16-bit instructions, compatible with the 808680286 microprocessors. This means that the instructions use 16-bit offset addresses and 16-bit registers by default. If D = 1, the instructions are 32-bits by default. Access rights byte: allows complete control over the segment by defining the privilege level and other information about the segment. BY UBAID SAUDAGAR
57
09-10-2012
Address calculation in protected mode In protected mode the address is formed in such a way that the selector (16 bit segment register) selects one of the many descriptors from the descriptor table. The descriptor contains base address of the segment and the limit (which defines the maximum size of segment). Base address is of 32 bits and limit is of 20 bits (therefore the maximum size of the segment is 1Mbyte) Now the linear address is formed by adding the 32 bit offset with 32 bit base address to get 32 bit linear address. BY UBAID SAUDAGAR
58
09-10-2012
Descriptor contains base address, limit and access rights
32 bit offset
16 bit selector
Selects one of the many descriptors
0
0H
1
8H
2
10h
3
18h
32 bit base address
+
. . . 8191
BY UBAID SAUDAGAR
32 bit linear address
fff8h
Global or Local descriptor table
59
= Physical address, since paging is not enabled
09-10-2012
Address calculation in protected mode
Offset is of 32 bits therefore the maximum size of the segment possible is 4 Gb. But limit size is 20 bits and which indicates that maximum segment size is of 1 Mbyte. In above case we notice that the granular bit in the descriptor is 0. Due to which the offset gets added to base address but the upper 12 bits of offset are all 0’s.
BY UBAID SAUDAGAR
60
09-10-2012
Paging mechanism The segmentation scheme may divide the physical memory into variable size segments but the paging divides the memory into fixed size pages.
The advantage of the paging scheme is that the complete segment of a task need not be in the physical memory at any time. Only a few pages of the segments, which are required currently for the execution need to available in the physical memory. Thus the memory requirement of the task is reduced, therefore remaining memory is used for other tasks. Whenever the other pages of the task are required for execution, they may be fetched from the secondary storage. The previous pages which are executed need not be available in the memory. BY UBAID SAUDAGAR
61
09-10-2012
Paging Mechanism A key advantage to memory paging is that memory allocated to a program does not have to be contiguous, and because of that, there is very little internal fragmentation. Example: Show memory page allocation for the following sequence: Program A requests 3 pages of memory. Program C requests 2 pages of memory. Program D requests 2 pages of memory. Program C terminates, leaving 2 empty pages. Program B requests 3 pages of memory, and it is allocated the 2 empty pages that program C left, plus an additional page after program D. BY UBAID SAUDAGAR
62
09-10-2012
Paging Mechanism
BY UBAID SAUDAGAR
63
09-10-2012
Address calculation when paging is enabled The 32-bit linear address generated by the segmentation unit can be optionally fed into the paging unit to undergo a second address manipulation process.
BY UBAID SAUDAGAR
64
09-10-2012
Descriptor contains base address, limit and access rights
32 bit offset
16 bit selector
Selects one of the many descriptors
0
0H
1
8H
2
10h
3
18h
32 bit base address
+
. .
32 bit linear address
. 8191 BY Ubaid by UBAIDSaudagar SAUDAGAR
fff8h
Global or Local descriptor table
65
Goes to paging unit
09-10-2012
Address calculation when paging is enabled In the above figure we notice that, the linear address is formed by combining the base address and the offset address. This is actually the physical address in case of segmentation which is used to access the segments. But in case of paging this linear address is applied to paging unit and then physical address is formed which accesses the pages. Lets see how physical address is formed on pg. 67
BY UBAID SAUDAGAR
66
09-10-2012
(Upper 10 bits) Offset within page directory
+ Page directory of 4 Kb 4 bytes
+
4 bytes
(12 bits) offset within pages
Pages
-
Base address
Linear address
4 bytes Base address
4 bytes
+
4 kb 4 kb
4 bytes -
(next 10 bits) offset within page tables Page tables of 4 Kb each
4 bytes
-
1024 entries, each entry is base address of page Each table table has 1024 entries, each UBAID SAUDAGAR entry points CR3BY gives the base address to a page
1024 page tables
4 bytes -
-
4 kb
4 bytes 4 bytes
Total number of pages = 1024 * 1024 =- 1048576 = 1M -
67
Offset address varies within a page = 0000 0000 0000 = 000 1 1 1 1 1 1 1 1 1 1 1 1 = FFF09-10-2012
Virtual address 801C3400H 10 0000 0000 (200H)
200h
01 1100 0011 (1C3H)
0100 0000 0000 (400H)
This physical address is used to access a page
000E4000h
00028000h
Physical address =
+ 00028400h
Base address BY UBAID SAUDAGAR
68
09-10-2012
Address calculation when paging is enabled A close examination of the paging process reveals that the processor breaks the linear address into three components before turning it into a physical one.
The top 10 bits of the linear address are used by the processor to index or point the page directory table. The next 10 bits of the linear address serve as an index into the corresponding page table. By adding the page table entry value that is actually the base address to the page and the offset which comes from the last 12 bits of linear address we can locate the requested physical address and send it to its address bus and access a page. BY UBAID SAUDAGAR
69
09-10-2012
Address calculation when paging is enabled The linear address obtained by combining the base address (obtained from descriptor) and offset address is split up into three parts by the MMU. The upper 10 bits are used to select the entries in the page directory. Page directory : The page directory contains 1024 page directory entries, each of which is 4 bytes (32 bits). This means the page directory is 4 K bytes long. There is only one page directory in memory and its base address is contained in CR3. With the help of base address page directory is selected and with the help of offset the entries in the page directory is selected. Imp: The total entries in the page directory are 1024. Therefore to access these entries we require 10 addressing bits which we get from the upper 10 bits of linear address. BY UBAID SAUDAGAR
70
09-10-2012
Address calculation when paging is enabled Therefore the 10 bits(offset) will vary as: 00 0000 0000 = 000 (hex) = 0 1 1 1 1 1 1 1 1 1 1 = 3FF (hex) = 1023 (decimal) Now each address will select an entry in the page directory table. But, each entry is of 4 bytes therefore total number no. of memory locations are: 1024 * 4 = 4096, therefore to address 4096 locations 12 bits are required hence the MMU appends two bits at the end and their value are always 00 Now the offset will vary as: 0000 0000 00 00 = 000 (hex) = 0th location 0000 0000 01 00 = 004 (hex) = 4th location 0000 0000 10 00 = 008 (hex) = 8th location First 10 bits 1 1 1 1 1 1 1 1 1 1 00 = FFC (hex) = 1024th location BY UBAID SAUDAGAR
71
09-10-2012
Address calculation when paging is enabled The next 10 bits are used to select the entries within the page tables. Page table: Page directory has 1024 entries and each entry selects a page table. Each page table contains 1024 page table entries, each of which is 4 bytes (32 bits). This means that each page table is 4 K bytes long. As such there are 1024 page tables and each table of 4Kb. Each page table entry is actually the base address to a page in the page frame. Therefore number of pages accessed or addressed are 1024 (1 page table entries) * 1024 (number of page tables) = 1048576 = 1 Mb pages. Note: The number of bits available as offset to move within the page table are 10 i.e. same as page directory, hence addressing is same as explained previously. BY UBAID SAUDAGAR
72
09-10-2012
Address calculation when paging is enabled The next 12 bits are used as offset to move within the pages of 4Kb. It is important to notice that 10 bits are used to address entries in the page directory(even though PD requires 4Kb of memory), 10bits are used to address entries in the page table (even though PT requires 4Kb of memory), 12 bits are required as offset to move within a page (even though page size is of 4Kb). This is because MMU appends 00 at the end of 10 bits hence it moves within a PD and PT and addresses 4kb of memory and only the entries which are 1024 for which only 10 bits are required. BY UBAID SAUDAGAR
73
09-10-2012
Address calculation when paging is enabled
Page: Each page table entry points to the starting physical address of a page in memory (i.e., the physical page number). In other words each entry in the page table acts as base address to a page and the 12 bits from the linear address acts as offset address. Number of pages accessed or addressed are 1024 (1 page table entries) * 1024 (number of page tables) = 1048576 = 1 Mb pages. 1M pages * 4K (size of each page) = 4Gb space = size of page frame
BY UBAID SAUDAGAR
74
09-10-2012
Note: The memory-management unit (MMU) within the 80386 is similar to the MMU inside the 80286, except that the 80386 contains a paging unit not found in the 80286. The MMU performs the task of converting linear addresses, as they appear as outputs from a program, into physical addresses that access a physical memory location located anywhere within the memory system.
BY UBAID SAUDAGAR
75
09-10-2012
Translation look aside buffer A translation look aside buffer (TLB) is a cache that memory management hardware uses to improve virtual address translation speed.
Since the page directory and page tables are of 4kb, it would be very inefficient to have to access them every time an address requires translation since two memory reads are needed to read the entries from each table. This requires n number of clock cycles. To improve performance, a 32-entry page table cache is provided which stores the 32 recently accessed page table entries. Whenever a linear address is to be converted to physical address, it is first checked to see, whether it corresponds to any of the page table cache entries. This page table cache is called as translation look-aside buffer (TLB) that automatically translate the upper 20 bits of the virtual address into upper 20 physical address bits. BY UBAID SAUDAGAR
76
09-10-2012
Translation look aside buffer 10 bits
10bits
12 bits (offset)
20 bits Valid virtual upper 20 bits physical upper 20 bits 0
TLB
0 0
+
1
Physical address
0 0 0 BY UBAID SAUDAGAR
0
77
09-10-2012
Translation look aside buffer Whenever a linear address is formed, it gets converted to physical address through 2 level paging (i.e. PD and PT). The resent addresses (linear and physical) are stored in the TLB. Thus from the above figure we see that the Translation look aside buffer (TLB) contains upper 20 bits of virtual address (linear address) as well as upper 20 bits of physical address. Whenever any page is to be accessed, this linear address needs to be converted again and again to physical address through 2 level paging. To avoid this and to access the most resent pages or to access some pages again and again quickly we use TLB. The linear address (virtual address) is stored in TLB along with its corresponding physical address, if the required linear address is available then it’s corresponding physical address is retrieved and combined with the offset to access the page. This happens in a single clock cycle. BY UBAID SAUDAGAR
78
09-10-2012
Control Registers
Figure below shows the format of the 80386 control registers CR0, CR2, and CR3. CR0 contains system control flags, which control or indicate conditions that apply to the system as a whole, not to an individual task.
BY UBAID SAUDAGAR
79
09-10-2012
Control registers 16 MSB P G
16 LSB
0---------------------------------------------------------------------------0 0-------------------------------------------------------------------------0 E T E M P T S M P E CR0 INTEL RESERVED
CR1
PAGE FAULT LINEAR ADDRESS
PAGE DIRECTORY BASE ADDRESS
BY UBAID SAUDAGAR
CR2
0000 0000 0000
80
CR3
09-10-2012
Control Registers Control Register (CR0): Machine Control Register As shown in figure, control register CR0 contains six defined bits for control and status purposes. The low order 16 bits of CR0 are also known as machine status word(MSW), for compatibility with 80286 protected mode. The defined CR0 bits are described below: BY UBAID SAUDAGAR
81
09-10-2012
Cont. PG (Paging, bit 31): If paging bit is 1/0, then paging is enabled/disabled from the on-chip paging unit. ET (Extension Coprocessor,bit4): If 0/1, then it indicates that the microprocessor 80386 is connected with the co-processor 80287/80387. The 80386 is designed to operate with either an 80287 or 80387 math coprocessor. The ET bit of CR0 indicates which type of coprocessor is present. ET is set automatically by the 80386 after RESET If ET is set, the 80386 uses the 32-bit protocol of the 80387; if reset, the 80386 uses the 16-bit protocol of the 80287. BY UBAID SAUDAGAR
82
09-10-2012
Cont.
TS(Task switch, bit 3): TS is automatically set whenever a task switch operation is performed. If TS = 1, then the µp will execute more than one program. If TS = 0, then µp will not performing task switching, i.e. not going to another program without executing first program. EM (Emulate Co-processor, bit 2): If EM = 1, then whenever Coprocessor instructions comes in the program then µp executes INT7 (exception 7). The ISR of INT7 is used to execute the operation of the co processor instructions using software. It will take nearly 100 times more time compared to the time required by the co processor. If EM = 0, then it allows the co processor opcodes to be actually executed on an actually 80387DX co processor (this is the default case after reset). BY UBAID SAUDAGAR
83
09-10-2012
Cont. MP (Monitor Processor extension (co - processor), bit 1 ): If MP = 1/0, then it indicates that co processor is present/not present respectively. When the co processor is connected to 80386, then there is no meaning of the EM bit, i.e. when MP = 1, then there is no use of EM. PE (Protection enable, bit 0): If PE = 1, then the 80386 gets defined from real mode to protected mode. If PE = 0, then 80386 again operates in real mode. BY UBAID SAUDAGAR
84
09-10-2012
Cont. Control register (CR1) : Intel Reserved It is reserved by Intel for used in future microprocessor IC’s Control register (CR2) : Page fault linear address If the paging unit is enabled, but if there is any fault in paging unit, then 32 bit linear address is saved in register CR2 and the µp executes exception (dedicated interrupt, INT14) to display the error message.
BY UBAID SAUDAGAR
85
09-10-2012
Cont. Control Register (CR3): Page directory base address A directory table points to the page table and page table points to page frame. Directory table is pointed by CR3 (i.e. the base address or starting address or root address of directory table is present in CR3) Note that this address locates the page directory at any 4K boundary in the memory system because it is appended internally with 000h.
BY UBAID SAUDAGAR
86
09-10-2012
Invisible register Every memory segment is associated with a descriptor. When other memory segment is to be selected, i.e. the next memory segment, the base address of previous one is automatically stored in invisible register (IR). The invisible register is operated by the microprocessor, i.e. the IR is unused by the programmer.
BY UBAID SAUDAGAR
87
09-10-2012
System address registers GDTR = Global Descriptor Table Register
LDTR = Local Descriptor Table Register TR = Task Register
BY UBAID SAUDAGAR
88
09-10-2012
Physical memory
GDTR GDTR
Since limit has 16 bits, size of GDT is 64kb
Descriptor 8191
Descriptor 8190 Descriptor 8189
Length of the GDT
47
16 15 Base address
0
-
Limit
Descriptor 1 BA
Descriptor 0
80386 microprocessor
BY UBAID SAUDAGAR
89
09-10-2012
GDTR GDT consist of descriptors which are available to almost all the task in the system The contents of the global descriptor table register define a table in the 80386DX's physical memory address space called the Global Descriptor Table (GDT). GDTR is a 48-bit register that is located inside the 80386DX. The lower two bytes of this register, which are identified as LIMIT, specify the size in byte of the GDT. Since LIMIT has 16 bits, the GDT can be up to 65,536 bytes long. The upper four bytes of the GDTR, which are labelled BASE, locate the beginning of the GDT in physical memory. This 32-bit base address allows the table to be positioned anywhere in the 80386DX's address space BY UBAID SAUDAGAR
90
09-10-2012
LDTR
Physical memory Descriptor 8191 -
15 LDTR
Descriptor n
0
GDT
-
Selector no. n
Descriptor 0 LDTR invisible or cache register 47 Base address
16 15
0
Descriptor 8191
Limit
Descriptor 1
LDT
Base address BY UBAID SAUDAGAR
91
Descriptor 0 09-10-2012
LDTR Firstly the main difference between GDT and LDT is that, GDT consist of descriptors which are global and LDT consist of those descriptors which are associated to a particular task.
Now the question arises how this LDT gets created? LDTR is a 16 bit selector which selects one of the descriptors from the GDT, from there it gets the base address and limit. In other words LDTR is a 16 bit selector which points to a LDT descriptor in the GDT. This 32 bit base address and 16 bit limit value are stored in a LDTR invisible register also called as cache register. Now this base address is the starting location of LDT in physical memory and limit defines the maximum size of the LDT. BY UBAID SAUDAGAR
92
09-10-2012
Task register (TR) The task register is one of the key elements in the protected mode task switching mechanism of the 80386DX microprocessor. This register holds a 16-bit index value called a selector. TR is used to locate a descriptor in the global descriptor table The initial selector must be loaded into TR under software control. This starts the initial task. After this is done, the selector is changed automatically whenever the 80386DX executes an instruction that performs a task switching. BY UBAID SAUDAGAR
93
09-10-2012
Debug registers 31
0 Breakpoint address 0
𝐷𝑅0
Breakpoint address 1
𝐷𝑅1
Breakpoint address 2
𝐷𝑅2
Breakpoint address 3
𝐷𝑅3
Intel reserved
𝐷𝑅4
Intel reserved Breakpoint status BY UBAID SAUDAGAR
94 control Breakpoint
𝐷𝑅5 𝐷𝑅6 09-10-2012
𝐷𝑅7
Debug registers
There are in all six debug registers which are accessible to the programmer and on chip support for debugging.
Debug registers 𝐷𝑅0 - 𝐷𝑅3 specify the four linear breakpoints. In other words, the addresses (32 bit address)where we place a breakpoint, that address is stored in these 4 registers. These addresses are constantly compared with the address generated by the program. If a match occurs then 80386 will cause type 1 interrupt (TRAP) indicating to stop executing in free run mode. Debug control register 𝐷𝑅7 is used to set the breakpoints. Debug status register 𝐷𝑅6 is used to check the current status of the breakpoints. BY UBAID SAUDAGAR
95
09-10-2012
Test registers
31
BY UBAID SAUDAGAR
0 Test command register
𝑇𝑅6
Test data register
𝑇𝑅7
96
09-10-2012
Test registers The Intel 386DX provides a mechanism for testing the TLB if desired. This particular mechanism is unique to Intel386 DX. Two test registers are used for testing mechanism viz. Test command register (𝑇𝑅6 ) and Test Data register (𝑇𝑅7 ). There are two TLB testing operations: 1. Write entries into the TLB 2. Perform TLB lookups When we need to test the TLB, paging must be turned off i.e. (PG = 0 in 𝐶𝑅0 ) to enable the TLB testing hardware and avoid interference with the test data being written to the TLB. BY UBAID SAUDAGAR
97
09-10-2012
Virtual 8086 mode of 80386 microprocessor In the real mode, µp works as a fast 8086. In the protected mode all the features of 80386 are available. But to come back to real mode, the only way was to reset the µp. Thus, the virtual 8086 mode of operation of 80386 offers an advantage of executing 8086 programs while in protected mode. Whenever we boot the µp, it is by default in the real mode. To go the protected mode the PE bit in CR0 is set to 1. Now we are in the protected mode, generally to go back to real mode the only way was to reset the µp, but now due to V8086 mode we can switch to real mode without reset. BY UBAID SAUDAGAR
98
09-10-2012
Virtual 8086 mode of 80386 microprocessor Virtual 8086 mode is entered by changing the VM bit in the EFLAG register to a logic 1. This mode is entered via an IRET instruction if the privilege level is 00. This bit cannot be set in any other manner. Therefore VM bit tells us that whether we are using 8086 instructions or 80386 instructions. The address forming mechanism in virtual 8086 mode is identical to that of 8086. The 80386 allows the operating system to specify which programs use 8086 style address mechanism and which programs use protected mode addressing. The virtual 8086 mode executes all the programs at privilege level 3 (the least privilege). BY UBAID SAUDAGAR
99
09-10-2012
Virtual 8086 mode of 80386 microprocessor TaskA of 80386
µp TaskC of 80386
TaskB of 8086
BY UBAID SAUDAGAR
100
09-10-2012
Virtual 8086 mode of 80386 microprocessor Consider the above example:
To execute task A we need to enter to enter in the protected mode as it is a 80386 program. Now when the processor switches to task B to execute 8086 program, programmer executes IRET instruction at privilege level 00 which sets the VM bit in the EFLAG register. BY UBAID SAUDAGAR
101
09-10-2012
Difference between 80286 and 80386 80286
80386
16 bit microprocessor Accessible memory: Physical memory = 16Mb Virtual memory = 1 Gb Address bus = 24 bits Data bus = 16 bits Paging mechanism not supported Control registers and test registers not present On chip debug registers not present To move from protected mode to real mode µp needs to be reset. BY UBAID SAUDAGAR
102
32 bit microprocessor Accessible memory: Physical memory = 4 Gb Virtual memory = 64 Tb Address bus = 32 bits Data bus = 32 bits Supports 2 level paging mechanism Control registers and test registers present On chip debug registers To move from protected mode to real mode VM bit in the EFLAG must be set i.e. VM =1 09-10-2012
Data types supported by 80386 Unsigned integer number
Byte
Word
Signed integer number
Unpacked BCD number
ASCII numbers or codes
Real numbers
Byte
9 in packed BCD is 1001
9 in unpacked BCD is 0000 1001
Short real number = 32 bit
Word
87 in packed BCD is 1000 0111
87 in packed BCD is 0000 1000 0000 0111
Long real number = 64 bit
Dword
Dword
Qword
Qword
BY UBAID SAUDAGAR
Packed BCD number
Temporary real number = 80 bit
103
09-10-2012
8086 Microprocessor Pdf

80386 Microprocessor Handbook Pdf
The architecture, organization and realization of the 80386 are discussed and compared with the previous models of the 86 family. Subsequently, four other 32-Bit new microprocessors (MC68020, NS32332, Z80000, WE32100) are briefly described and compared with the 80386. . Flag Register of 80386: The Flag register of 80386 is a 32 bit register. Out of the 32 bits, Intel has reserved bits D18 to D31, D5 and D3, while D1 is always set at 1.Two extra new flags are added to the 80286 flag to derive the flag register of 80386. They are VM and RF flags. Register Organisation (cont.). INTEL 80386 PROGRAMMER'S REFERENCE MANUAL 1986 Page 1 of 421 INTEL 80386 PROGRAMMER'S REFERENCE MANUAL 1986 Intel Corporation makes no warranty for the use of its products and assumes no responsibility for any errors which may appear in this document nor does it make a commitment to update the information contained herein.
